Network + practice questions n10-008 – Kickstarting with Network+ practice questions N10-008, we embark on a journey of knowledge and preparation. This comprehensive guide delves into the intricacies of networking fundamentals, providing an in-depth understanding of the concepts and technologies that underpin modern networks.
As we navigate through the chapters, we will explore the OSI model, TCP/IP protocol suite, network topologies, network hardware, network security, network troubleshooting, network management, network design, network protocols, network performance, network virtualization, and network automation. Each topic is presented with clarity and precision, ensuring a thorough grasp of the subject matter.
Network Basics
Networks are the backbone of modern communication and information exchange. Understanding the fundamentals of networking is essential for anyone working in the IT industry. This section provides a comprehensive overview of network basics, covering the OSI model, TCP/IP protocol suite, and different types of network topologies.
OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that divides the communication process into seven layers. Each layer has specific responsibilities and interacts with adjacent layers to facilitate data transmission.
- Physical Layer:Transmits raw data bits over a physical medium.
- Data Link Layer:Groups bits into frames and adds error-checking mechanisms.
- Network Layer:Routes data packets through the network.
- Session Layer:Establishes, manages, and terminates communication sessions.
- Presentation Layer:Translates data into a format that is compatible with the application.
- Application Layer:Provides services and interfaces to the end-user applications.
li> Transport Layer:Ensures reliable data delivery and manages flow control.
TCP/IP Protocol Suite
The TCP/IP (Transmission Control Protocol/Internet Protocol) suite is a set of protocols that governs communication over the internet and other networks. It consists of four layers:
- Network Interface Layer:Responsible for sending and receiving data at the physical level.
- Internet Layer:Provides routing and addressing mechanisms.
- Transport Layer:Ensures reliable data delivery using TCP or UDP protocols.
- Application Layer:Supports various applications, such as web browsing, email, and file transfer.
Network Topologies
A network topology refers to the physical arrangement of devices within a network. Common topologies include:
- Bus Topology:All devices are connected to a single shared transmission medium.
- Star Topology:Devices are connected to a central hub or switch.
- Ring Topology:Devices are connected in a circular fashion, with each device connected to two others.
- Mesh Topology:Each device is connected to multiple other devices, creating a fully interconnected network.
Network Hardware

Network hardware plays a crucial role in connecting devices and facilitating communication within a network. These devices perform specific functions to ensure the smooth and efficient transmission of data.
Routers
Routers are responsible for directing network traffic between different networks or subnets. They use routing tables to determine the best path for data to take based on the destination address. Routers also perform network address translation (NAT), allowing devices on different networks to communicate using different IP addresses.
Switches
Switches operate at the data link layer of the OSI model. They connect multiple devices within a single network segment and forward frames based on their MAC addresses. Switches provide higher bandwidth and lower latency compared to hubs, making them suitable for modern networks.
Firewalls
Firewalls act as security devices that monitor and control incoming and outgoing network traffic. They enforce security policies to prevent unauthorized access, protect against cyber threats, and maintain the confidentiality and integrity of network data. Firewalls can be hardware-based, software-based, or a combination of both.
Network Interface Cards (NICs)
Network interface cards (NICs) are hardware components that connect individual devices to a network. They provide the physical interface for data transmission and reception. NICs are typically installed in expansion slots on computers or embedded in network devices such as routers and switches.
Network Cables
Network cables are physical media used to connect network devices and transmit data. Different types of network cables have varying characteristics, such as bandwidth, distance limitations, and shielding.
- Unshielded twisted pair (UTP) cables are commonly used in home and office networks.
- Shielded twisted pair (STP) cables provide better protection against electromagnetic interference (EMI) and are often used in industrial environments.
- Coaxial cables are used for long-distance connections and are often employed in cable television networks.
- Fiber optic cables transmit data using light pulses and offer high bandwidth and low latency, making them suitable for high-speed networks.
Network Security
Network security is a critical aspect of maintaining the confidentiality, integrity, and availability of data and resources on a network. It involves protecting against unauthorized access, data breaches, and other security threats.
Common network security threats include:
- Malware: Malicious software that can damage or steal data.
- Phishing: Attempts to trick users into revealing sensitive information.
- Denial-of-service (DoS) attacks: Overwhelming a network with traffic to prevent legitimate users from accessing it.
Network security principles include:
- Confidentiality: Ensuring that only authorized users can access data.
- Integrity: Protecting data from unauthorized modification.
- Availability: Ensuring that authorized users can access data when needed.
Best practices for network security include:
- Using strong passwords and multi-factor authentication.
- Installing and maintaining firewalls and intrusion detection systems.
- Regularly patching software and firmware.
- Educating users about security risks.
Network Security Controls
Network security controls are mechanisms used to protect networks from threats. Types of network security controls include:
- Physical controls: Physical barriers, such as fences and security guards, that prevent unauthorized access to network infrastructure.
- Technical controls: Software and hardware technologies, such as firewalls and intrusion detection systems, that monitor and block unauthorized access to networks.
- Administrative controls: Policies and procedures that define how networks are managed and used, such as password policies and access control lists.
Network Troubleshooting: Network + Practice Questions N10-008
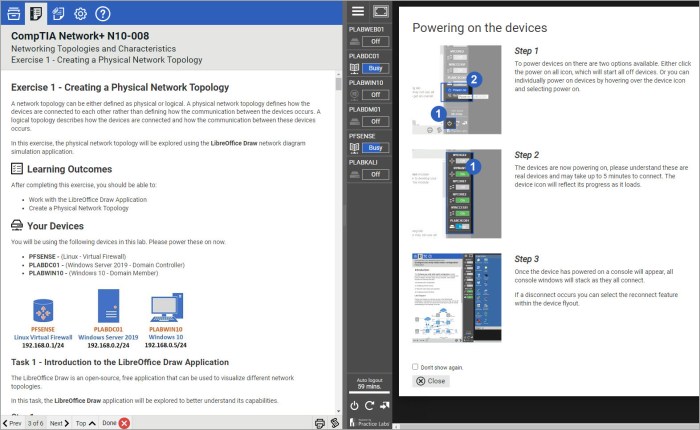
Network troubleshooting is the process of identifying and resolving network issues. It involves a systematic approach to diagnose and fix problems that affect network performance and connectivity.The steps involved in troubleshooting network issues typically include:
- Identifying the symptoms of the problem, such as slow network speeds, dropped connections, or inability to access certain resources.
- Gathering information about the network, including its topology, hardware, and software configurations.
- Analyzing the gathered information to identify potential causes of the problem.
- Testing and implementing solutions to resolve the problem.
- Verifying that the solution has resolved the problem and monitoring the network to ensure that it remains stable.
Network monitoring tools can be used to assist in troubleshooting network issues. These tools provide real-time visibility into network performance and can help identify potential problems before they cause significant disruptions.Common network problems and their solutions include:
- Slow network speeds can be caused by a variety of factors, such as congested network traffic, outdated hardware, or incorrect network configurations. Solutions include upgrading network hardware, optimizing network traffic, and fine-tuning network configurations.
- Dropped connections can be caused by faulty network cables, loose connections, or interference from other devices. Solutions include replacing faulty cables, tightening loose connections, and eliminating sources of interference.
- Inability to access certain resources can be caused by firewall restrictions, incorrect DNS configurations, or problems with the destination server. Solutions include adjusting firewall settings, configuring DNS correctly, and troubleshooting the destination server.
Network Management
Network management plays a crucial role in ensuring the efficiency, reliability, and security of computer networks. It involves the systematic administration and monitoring of network resources, such as devices, applications, and services, to maintain optimal performance and availability.
Network management encompasses various tasks, including:
Network Monitoring
- Continuously monitoring network devices and traffic to detect and resolve potential issues proactively.
- Using monitoring tools to collect and analyze data on network performance, such as bandwidth utilization, latency, and error rates.
- Establishing performance baselines and thresholds to identify anomalies and trigger alerts.
Fault Management
- Responding to and resolving network failures and outages promptly.
- Identifying the root cause of network problems and implementing appropriate solutions.
- Performing root cause analysis to prevent similar issues from recurring.
Configuration Management
- Managing and updating network device configurations to ensure consistent and optimal performance.
- Using configuration management tools to automate configuration tasks and maintain a centralized repository of device settings.
- Implementing change management processes to control and track configuration changes.
Security Management
- Implementing and maintaining network security measures to protect against threats and vulnerabilities.
- Monitoring network traffic for suspicious activity and implementing appropriate security controls.
- Educating users on network security best practices and enforcing security policies.
Performance Management
- Optimizing network performance by identifying and resolving bottlenecks.
- Using performance management tools to analyze network traffic patterns and identify areas for improvement.
- Implementing traffic engineering techniques to optimize network utilization and reduce congestion.
Network Management Tools, Network + practice questions n10-008
Network management tools are essential for effective network management. These tools provide a centralized platform for monitoring, managing, and troubleshooting network devices and services. Common network management tools include:
- Network monitoring systems
- Configuration management tools
- Security management tools
- Performance management tools
- Fault management systems
Network Design
Network design involves planning, implementing, and managing a computer network infrastructure to meet the specific needs and objectives of an organization or individual. It encompasses the selection of network components, topologies, protocols, and security measures to ensure efficient, reliable, and secure data communication.
Principles of Network Design
- Modularity:Breaking down the network into smaller, manageable components that can be easily added, removed, or modified.
- Scalability:Designing the network to accommodate future growth and changes in network requirements.
- Reliability:Implementing redundant components and failover mechanisms to ensure continuous network operation in the event of component failures.
- Security:Incorporating security measures to protect the network from unauthorized access, data breaches, and other threats.
- Cost-effectiveness:Optimizing the network design to minimize costs while meeting performance requirements.
Types of Network Designs
Common network designs include:
- Bus Topology:A simple design where all devices are connected to a single shared transmission medium.
- Star Topology:A design where all devices are connected to a central hub or switch.
- Ring Topology:A design where devices are connected in a circular fashion, with each device connected to two other devices.
- Mesh Topology:A design where all devices are interconnected with multiple paths, providing redundancy and high reliability.
Factors to Consider When Designing a Network
When designing a network, several factors need to be considered:
- Network Purpose and Requirements:Defining the specific objectives and performance requirements of the network.
- Network Size and Scope:Determining the number of devices, geographic coverage, and potential for future expansion.
- Budgetary Constraints:Establishing a budget and exploring cost-effective solutions that meet the required performance levels.
- Physical Constraints:Considering the physical environment, cable lengths, and potential obstacles that may impact network design.
- Security Considerations:Identifying potential security threats and implementing appropriate security measures to mitigate risks.
Network Protocols
Network protocols are a set of rules and procedures that govern how data is transmitted and received over a network. They define the format of the data, the method of transmission, and the error-checking mechanisms used.
There are many different types of network protocols, each designed for a specific purpose. Some of the most common network protocols include:
- HTTP (Hypertext Transfer Protocol):HTTP is the protocol used to transfer web pages and other files over the internet. It is a request-response protocol, where a client sends a request to a server, and the server sends back a response.
- FTP (File Transfer Protocol):FTP is the protocol used to transfer files between computers. It is a client-server protocol, where a client connects to a server and sends commands to transfer files.
- DNS (Domain Name System):DNS is the protocol used to translate domain names into IP addresses. It is a hierarchical system, where each level of the hierarchy is responsible for a different part of the domain name.
Network protocols play a vital role in network communication. They ensure that data is transmitted and received in a reliable and efficient manner. Without network protocols, it would be impossible to communicate over a network.
Network Performance
Network performance is a critical factor in the overall effectiveness of any network. It affects the speed, reliability, and security of data transmission. There are a number of factors that can affect network performance, including:
- Bandwidth: The amount of data that can be transmitted over a network connection at a given time.
- Latency: The time it takes for data to travel from one point to another on a network.
- Packet loss: The number of packets that are lost in transit due to errors or congestion.
- Jitter: The variation in the delay of packets as they travel across a network.
There are a number of different methods for measuring network performance. These include:
- Ping: A simple tool that measures the latency and packet loss between two points on a network.
- Traceroute: A tool that shows the path that packets take from one point to another on a network, and the latency and packet loss at each hop.
- Bandwidth testing: A tool that measures the amount of data that can be transmitted over a network connection at a given time.
There are a number of techniques that can be used to improve network performance. These include:
- Increasing bandwidth: This can be done by upgrading to a higher-speed network connection or by adding more bandwidth to an existing connection.
- Reducing latency: This can be done by optimizing the routing of packets, or by using a faster network connection.
- Minimizing packet loss: This can be done by using error correction techniques, or by using a more reliable network connection.
- Reducing jitter: This can be done by using a more reliable network connection, or by using a jitter buffer.
Network Virtualization

Network virtualization is the process of creating virtual networks on top of physical network infrastructure. This allows multiple virtual networks to run on the same physical network, each with its own set of security and performance characteristics.Network virtualization technologies can be divided into two main types:
-
-*Software-defined networking (SDN)
SDN decouples the control plane from the data plane, allowing network administrators to manage and provision networks programmatically.
-*Network function virtualization (NFV)
NFV virtualizes network functions, such as firewalls and load balancers, into software that can run on standard servers.
Network virtualization offers a number of benefits, including:
-
-*Increased flexibility
Virtual networks can be created and modified quickly and easily, without the need to reconfigure physical infrastructure.
-*Improved security
Virtual networks can be isolated from each other, which can help to improve security and compliance.
-*Reduced costs
Virtualization can help to reduce costs by consolidating multiple networks onto a single physical infrastructure.
However, network virtualization also poses some challenges, including:
-
-*Complexity
Virtual networks can be more complex to manage than physical networks.
-*Performance
Virtualization can introduce performance overhead, which can impact the performance of applications that rely on the network.
-*Security
Virtual networks can be more vulnerable to security attacks than physical networks.
Network Automation
Network automation refers to the use of software-defined tools and technologies to automate network management and configuration tasks. It streamlines network operations, reduces human error, and improves overall network efficiency and performance.
Benefits of Network Automation
- Increased Efficiency:Automation eliminates repetitive and time-consuming manual tasks, freeing up network administrators for more strategic initiatives.
- Reduced Errors:Automated processes are less prone to human error, leading to more reliable and stable network operations.
- Improved Performance:Automated systems can continuously monitor and optimize network performance, ensuring optimal network utilization and responsiveness.
- Enhanced Security:Automation can strengthen network security by automating security configurations, threat detection, and response mechanisms.
- Cost Savings:By reducing the need for manual labor and increasing efficiency, network automation can lead to significant cost savings.
Types of Network Automation Tools
- Configuration Management Tools:These tools automate the configuration and management of network devices, such as routers, switches, and firewalls.
- Monitoring and Analytics Tools:These tools provide real-time monitoring and analytics of network performance, allowing administrators to identify and resolve issues proactively.
- Orchestration and Provisioning Tools:These tools automate the deployment and management of network services, including the provisioning of new devices and services.
- Security Automation Tools:These tools automate security tasks, such as threat detection, incident response, and vulnerability management.
Challenges of Implementing Network Automation
- Complexity:Implementing network automation requires careful planning and integration with existing systems, which can be complex and time-consuming.
- Skill Gap:Network administrators need to develop new skills and expertise to manage and maintain automated systems.
- Cost:Implementing network automation can require significant upfront investment in software and training.
- Security Risks:Automated systems can introduce new security vulnerabilities if not implemented properly.
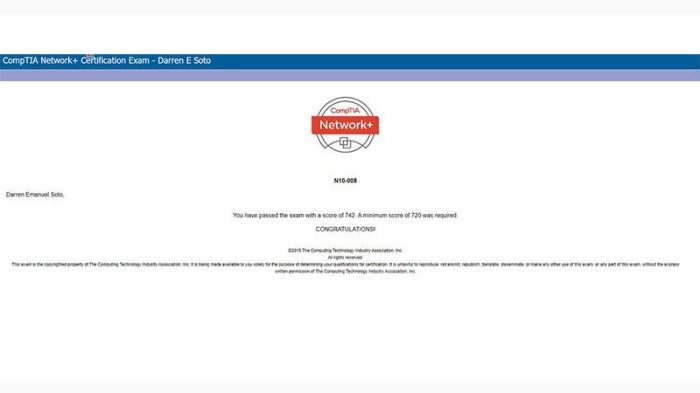
Expert Answers
What is the OSI model?
The OSI model (Open Systems Interconnection model) is a conceptual framework that describes how data is transmitted across a network. It consists of seven layers: physical, data link, network, transport, session, presentation, and application.
What is the TCP/IP protocol suite?
The TCP/IP protocol suite is a set of communication protocols that are used to transmit data over the internet. It includes protocols such as TCP (Transmission Control Protocol), IP (Internet Protocol), UDP (User Datagram Protocol), and ICMP (Internet Control Message Protocol).
What are the different types of network topologies?
The three main types of network topologies are bus, star, and ring. In a bus topology, all devices are connected to a single cable. In a star topology, all devices are connected to a central hub or switch. In a ring topology, all devices are connected to each other in a circular fashion.